What is DMARC Policy?
DMARC policy is a set of rules that domain owners publish in their DNS records to instruct receiving mail servers on how to handle emails that fail DMARC authentication checks.
Email security has become increasingly crucial in today's digital landscape, and DMARC (Domain-based Message Authentication, Reporting, and Conformance) stands at the forefront of protecting both senders and recipients from email-based threats.
What is DMARC: The Basics
DMARC is an email authentication protocol that helps organizations protect their domain from unauthorized use, commonly known as email spoofing and phishing attacks. It builds upon existing email authentication mechanisms and provides clear instructions on how to handle emails that fail authentication checks.
The importance of DMARC cannot be overstated:
- Prevents domain spoofing and phishing attempts
- Improves email deliverability rates
- Provides visibility into email authentication results
- Protects brand reputation and customer trust
What is DMARC Policy?
DMARC policy is a set of rules that domain owners publish in their DNS records to instruct receiving mail servers on how to handle emails that fail DMARC authentication checks. The policy specifies whether to monitor, quarantine, or reject such emails.
The DMARC policy is defined in the DMARC record, which is a DNS TXT record that includes various tags and values. The most critical tag is the "p" tag, which indicates the policy type. The three main DMARC policies are:
- p=none: Monitoring mode - no action taken on failing messages
- p=quarantine: Suspicious emails are sent to the spam folder
- p=reject: Failed messages are completely blocked
Key Components of a DMARC Record
A DMARC record consists of several crucial elements:
Required Tags:
- Version (v=DMARC1)
- Policy (p=none/quarantine/reject)
Optional but Important Tags:
- Reporting options (rua=, ruf=)
- Subdomain policy (sp=)
- Percentage of messages (pct=)
- Authentication alignment (aspf=, adkim=)
Here's a practical example of a basic DMARC record:
v=DMARC1; p=reject; rua=mailto:reports@example.com; pct=100
This record tells receiving servers to reject all failed messages and send aggregate reports to the specified email address.
Understanding these components is essential for implementing an effective DMARC policy. Start with a monitoring policy (p=none) to gather data about your email ecosystem, then gradually strengthen your policy as you gain confidence in your email authentication setup.
Remember that DMARC implementation is not a one-time task but rather an ongoing process that requires regular monitoring and adjustment based on the reports received and your organization's evolving needs.
Types of DMARC Policies Explained
Understanding DMARC policies is crucial for modern email security. These policies act as explicit instructions telling receiving mail servers how to handle emails that fail DMARC authentication. We'll be checking the different types of DMARC policies and understand which one might work best for your organization.
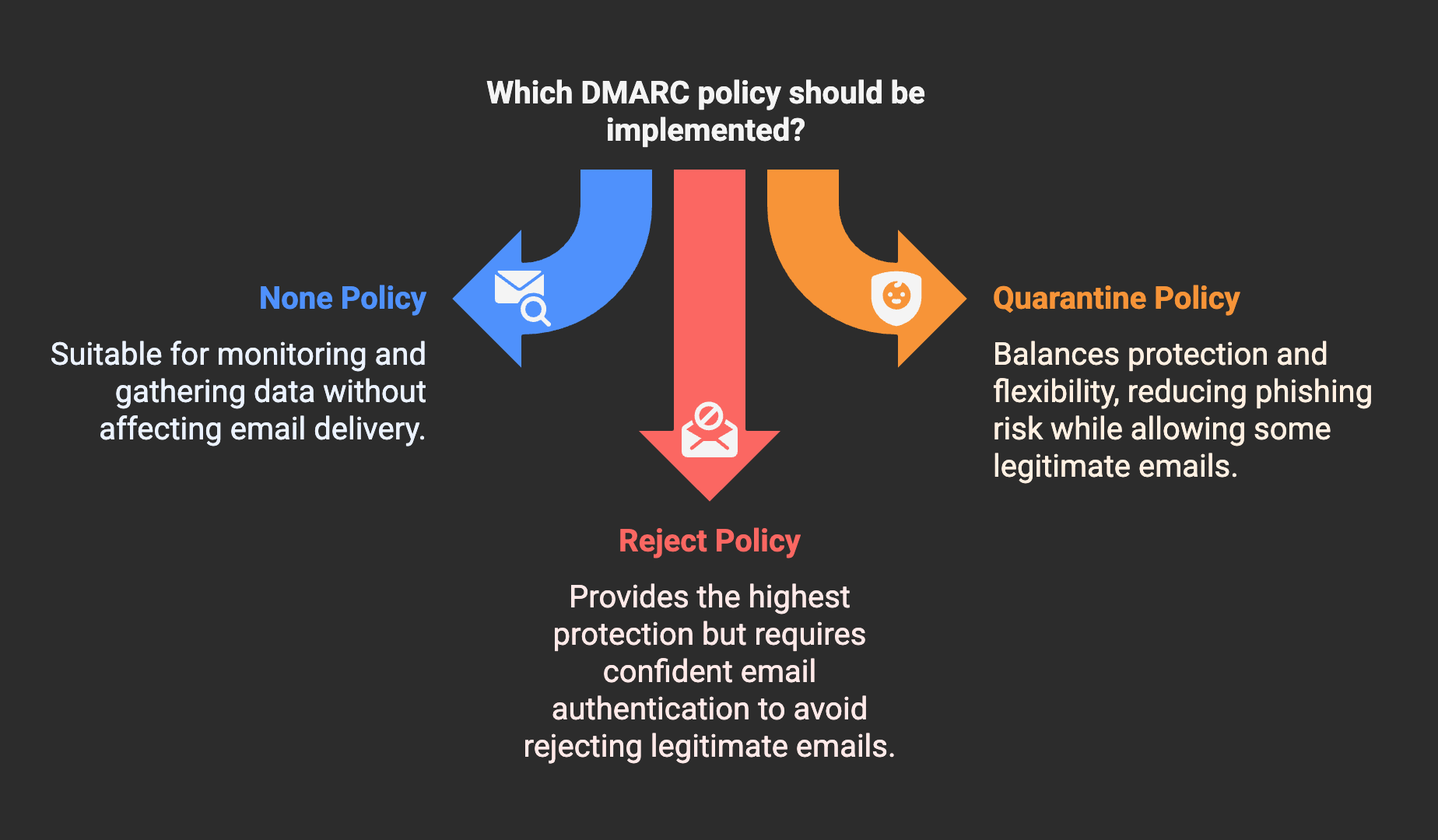
None Policy (p=none): Monitoring Mode
The 'none' policy is your starting point in the DMARC implementation journey. Think of it as wearing training wheels while learning to ride a bike – it's safe and informative without any risk.
Key characteristics of p=none:
- Doesn't affect email delivery
- Generates detailed reports about email authentication
- Perfect for initial DMARC deployment
- Helps identify legitimate email sources
For example, if you set p=none in your DMARC record, an email failing authentication will still reach the recipient's inbox, but you'll receive reports about it. This monitoring phase is essential for understanding your email ecosystem without disrupting business communications.
Quarantine Policy (p=quarantine): Suspicious Email Filtering
Moving up the security ladder, the quarantine policy adds a layer of protection while maintaining some flexibility. It's like having a bouncer who sends suspicious guests to a holding area instead of turning them away immediately.
When implementing p=quarantine:
- Suspicious emails typically land in spam folders
- Recipients can still access messages if needed
- Reduces the risk of email-based attacks
- Provides a balance between security and accessibility
For instance, if marketing emails from your third-party service provider fail DMARC checks, they'll be quarantined rather than blocked entirely, giving you time to fix authentication issues.
Reject Policy (p=reject): Maximum Protection
The reject policy is the security equivalent of a fortress wall – it's the strongest DMARC policy available. When asking "Which DMARC policy is best?" many security experts point to p=reject as the gold standard for organizations ready for strict enforcement.
Benefits of implementing p=reject:
- Complete blocking of unauthorized emails
- Maximum protection against spoofing attempts
- Clear-cut policy enforcement
- Strongest defense against phishing attacks
Real-world application: A financial institution using p=reject would ensure that any email claiming to be from their domain but failing authentication is immediately blocked, never reaching intended recipients.
Comparing Different DMARC Policy Types
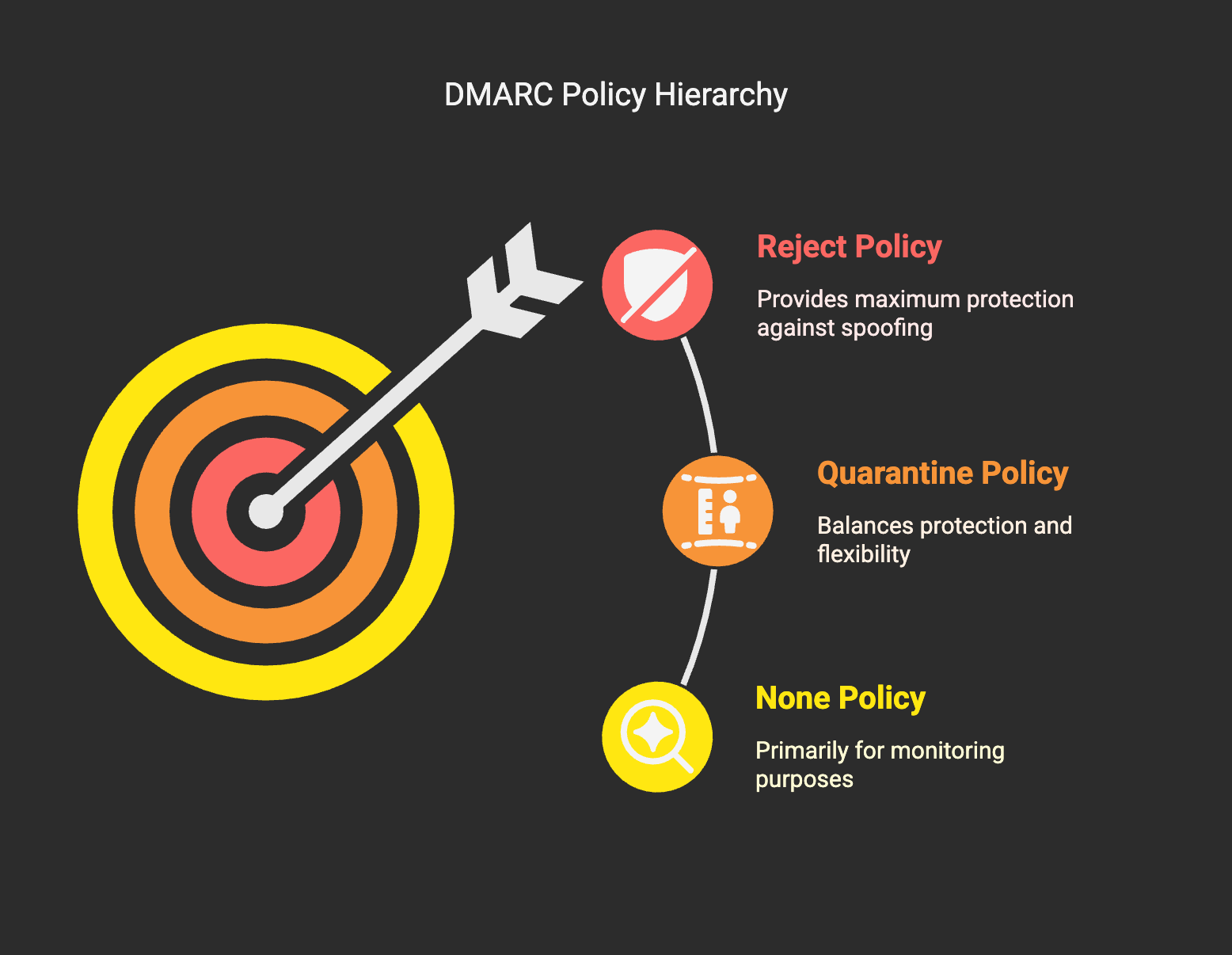
Why are DMARC policies important? The answer lies in their progressive approach to security. Think of DMARC policies as a three-step security ladder:
-
None (Monitoring)
- Risk Level: Low
- Implementation Difficulty: Easy
- Best for: Initial deployment and analysis
-
Quarantine (Filtering)
- Risk Level: Medium
- Implementation Difficulty: Moderate
- Best for: Organizations transitioning to stronger security
-
Reject (Blocking)
- Risk Level: High
- Implementation Difficulty: Complex
- Best for: Organizations requiring maximum security
How to decide on the right DMARC Policy?
TLDR: There's no one-size-fits-all DMARC policy. The best DMARC policy for your organization depends on your specific needs, email infrastructure, and security requirements.
What we can suggest is a policy progression strategy that can help you understand and slowly increase the security of your email infrastructure while also keeping the domain reputation and keeping deliverability.
Policy Progression Strategy (Recommended)
For optimal results, follow this strategic progression:
-
Initial Monitoring Phase (1-3 months)
- Deploy "p=none" policy
- Collect and analyze reports (Use Free DMARC Analyzer)
- Identify legitimate email sources
-
Quarantine Testing (2-4 months)
- Apply "p=quarantine" to subdomains first
- Monitor for issues
- Address any legitimate email failures
-
Full Enforcement (4-6 months)
- Gradually transition to "p=reject"
- Implement for critical domains first
- Maintain monitoring and adjustment
Remember that DMARC policy implementation is not a one-time task but an ongoing process that requires regular monitoring and adjustments. The best DMARC policy for your organization will depend on your specific needs, infrastructure, and security requirements.
Pro Tip: Always maintain a backup plan and be prepared to quickly modify policies if legitimate email delivery is affected. Consider implementing changes during low-traffic periods to minimize potential business impact.